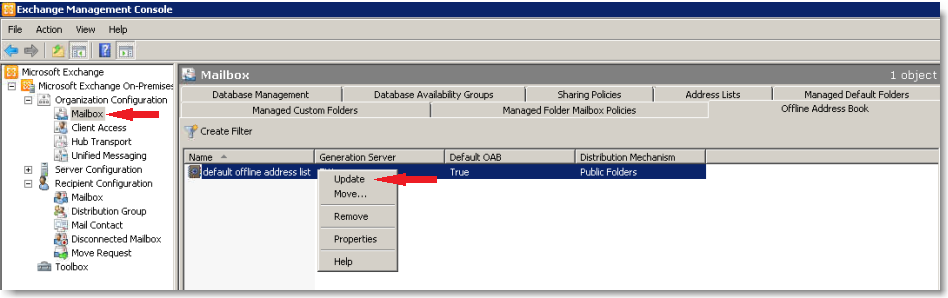
SonicWALL Hardware Failover/Load Balancing
With businesses today relying more and more on their Internet connection for critical email and cloud-based services, there is a growing need for providing hardware and ISP redundancy to ensure continuous uptime even in event of a hardware or ISP failure. The SonicWALL security appliance performs physical monitoring only on the Primary and Secondary WAN interfaces, meaning it only marks a WAN interface as Failed if the interface is disconnected or stops receiving an Ethernet-layer signal. For this reason, please see my next post to enable Probe Monitoring to cover all your bases in the event of a routing failure.
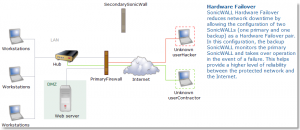
Due to this demand, two SonicWALL PRO appliances may run in Hardware Failover mode, which will provide security and connectivity in the event that one SonicWALL or an ISP becomes unstable or unavailable. In addition, SonicOS Enhanced firmware supports the ability to create multiple WAN interfaces (XO, X3), which can provide the use of multiple Internet connections either simultaneously or as a backup.
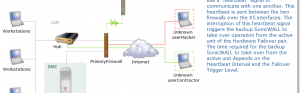
WAN Failover and Load Balancing allows you to designate the one of the user-assigned interfaces as a Secondary or backup WAN port. The secondary WAN port can be used in a simple active/passive setup, where traffic is only routed through the secondary WAN port if the primary WAN port is down and/or unavailable. This feature is referred to as basic failover. This allows the SonicWALL security appliance to maintain a persistent connection for WAN port traffic by failing over to the secondary WAN port. The primary and secondary WAN ports can also be used in a more dynamic active/active setup, where the administrator can choose a method of dividing outbound traffic flows between the Primary fixed WAN port and the user-assigned Secondary WAN port. This latter feature is referred to as load balancing.
WAN Failover and Load Balancing applies to outbound-initiated traffic only; it cannot be used to perform inbound Load Balancing functions, such as what a content switching or Load Balancing appliance provides.
Make sure that the SonicWALL appliance has the proper NAT policies for the Secondary WAN interface. An incorrect or missing NAT Policy for the Secondary WAN port is the most common problem seen when configuring WAN Failover & Load Balancing.
The Primary and Secondary WAN ports cannot be on the same IP subnet; each WAN connection must be on unique IP subnets in order to work properly.
You cannot use the WAN failover feature if you have configured the SonicWALL security appliance to use Transparent Mode in the Network > Interfaces page.
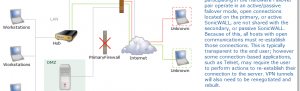
When you establish a connection with a WAN, you can create multiple interfaces, dividing up the task load over these interfaces. There are both Primary and Secondary WAN interfaces. This task distribution model maintains high performance, ensuring that one interface does not become an impasse to the point where it blocks traffic from passing. This process is WAN Load Balancing. While WAN Load Balancing addresses performance challenges, it can create other problems, including losing track of sessions. Session confusion can occur because some applications fail to adequately track multiple user sessions Load Balanced on multiple interfaces. These applications treat incoming packets as originating from different users because they use IP addresses to differentiate user sessions instead of application-layer user identification tags. To ensure that you have proper connectivity in all applications, SonicWALL provides a feature called Source and Destination IP addresses Binding, a solution that maintains a consistent mapping of traffic flows with a single outbound WAN interface.
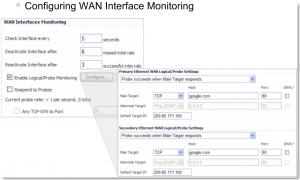
Primary WAN Ethernet Interface: X1 should normally be the selection.
Secondary WAN Ethernet Interface: If there are multiple possible secondary WAN interfaces, select the WAN Interface to be used for Failover and Load Balancing. X3 should normally be the selection.
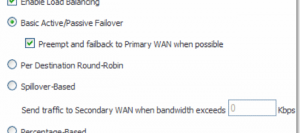
By default the Enable Load Balancing check box is selected. The SonicWALL will select Basic Active/Passive Failover as the method, but there are several load balancing methods available:
Basic Active/Passive Failover: When selected, the SonicWALL security appliance only sends traffic through the Secondary WAN interface if the Primary WAN interface has been marked inactive. The SonicWALL security appliance is set to use this as the default load balancing method. If the Primary WAN fails, then the SonicWALL security appliance reverts to this method.
Preempt and fail back to Primary WAN when possible: When this check box is selected, the SonicWALL security appliance switches back to sending its traffic across the Primary WAN interface when it either resumes responding to the SonicWALL security appliances when the WAN’s physical link is restored or the logical probe targets on the WAN port resume responding.
Per Destination Round-Robin: When selected, the SonicWALL security appliance Load Balances outgoing traffic on a per-destination basis. This is a simple load balancing method and, though not very granular, allows you to utilize both links in a basic fashion. Please note this feature will be overridden by specific static route entries.
Spillover-Based: When selected, the SonicWALL administrator can specify when the SonicWALL security appliance starts sending traffic through the Secondary WAN interface. This method allows the SonicWALL administrator to control when and if the Secondary interface is used. This method is used if you do not want outbound traffic sent across the Secondary WAN unless the Primary WAN is overloaded. The SonicWALL security appliance has a non-Management Interface exposed hold timer set to 20 seconds – if the sustained outbound traffic across the Primary WAN interface exceeds the administrator-defined bits per second (bps), then the SonicWALL security appliance spills outbound traffic to the Secondary WAN interface (on a per-destination basis). Please note this feature is overridden by specific static route entries.
Percentage-Based: When selected, you can specify the percentages of traffic sent through the Primary WAN and Secondary WAN interfaces. This method allows you to actively utilize both Primary and Secondary WAN interfaces. Please note this feature is overridden by specific static route entries.
Use Source and Destination IP Address Binding: When this checkbox is selected, it enables you to maintain a consistent mapping of traffic flows with a single outbound WAN interface, regardless of the percentage of traffic through that interface. Therefore, the outbound IP address of the connection remains consistent. However the percentage of traffic in each WAN interface may not match the percentage you specify in the Primary WAN Percentage field. This method uses only the source IP address and the destination IP address to determine when to bind a connection to a single interface and ignores all other information, such as source and destination TCP port numbers.